In response to a rapidly expanding attack surface (and increasingly sophisticated bad actors), the cybersecurity industry has embraced Zero Trust Architecture (ZTA). ZTA is a security framework that assumes all users, systems, and processes are potentially malicious — and thus require strict access control, regular monitoring, and a variety of preventative strategies (multi-factor authentication, micro-segmentation, identity protection, etc.)
An important step along the journey to Zero Trust is the implementation of what’s known as role-based access control, or RBAC for short. RBAC helps organizations apply principles of least privilege access (one of the fundamentals of ZTA) by controlling areas like:
- Which features users can access
- Which projects users can access
- Whether users can edit organization- or team-wide settings
- Whether users can edit projects
With an eye on helping our customers implement Zero Trust principles across their tech stack, FOSSA is pleased to be able to offer granular, role-based access control. In this blog, we’ll highlight the specific features of FOSSA RBAC — and how your organization can take advantage of them.
Note: The Biden Administration’s cybersecurity executive order includes a provision that requires the federal government to “advance toward Zero Trust Architecture,” which has only accelerated the industry’s transition to Zero Trust.
Organization Roles
FOSSA’s RBAC offers two different roles: organization and team. Organization Roles have access to all projects in your organization and/or permission to manage organization-level settings, such as billing information. (This is in contrast to Team Roles, which allow access to only specific teams and projects.)
There are four different types of organization roles, which are outlined in the table below.
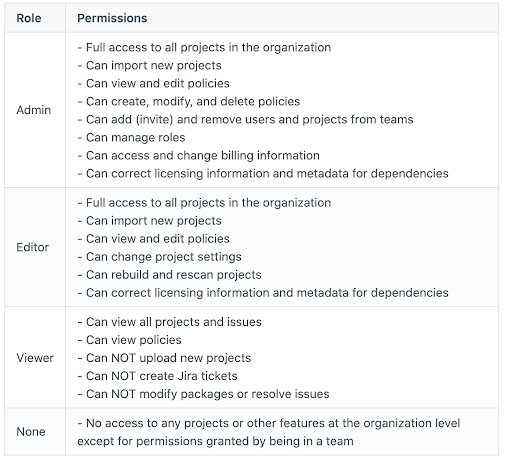
If a user is assigned the “none” role, they will only have access to assigned projects — not organization-level features or settings.
Team Roles
Team Roles give users the option to manage permissions and access on a team-by-team and project-by-project basis. They also enable administrators to create release groups, which limits access to outgoing reports (i.e. reports in products.) Team Roles do not include access to organizational-wide features, like policies or billing information.
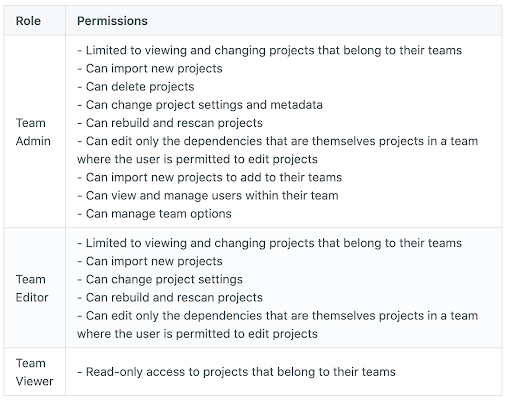
Organizations can select from one of three types of Team Roles: Admin, Editor, or Viewer.
Team Roles can also be used in due diligence situations (i.e. pre-M&A) to limit access to certain scans.
It’s important to note that while Team Admins and Team Editors can access the metadata in their projects, they generally cannot edit dependencies (because an edit to a dependency applies across the organization). In most cases, users who want to edit dependencies must have an organization-level role.
Custom Roles
Different security teams have different access control preferences, which is why FOSSA’s RBAC allows for the creation of custom roles at both the organization and team level.
Once you select the type of role (organization or team), you’ll be able to pick and choose from a list of permissions. For example, you could assign a user a Team Role with permissions to import new projects, but not to change project settings. Or, you could assign a user an Organization Role with permissions to access all projects across the organization and import new projects — but not to access billing information.
More on FOSSA RBAC
FOSSA role-based access control is currently available only to paying enterprise users. If you currently use FOSSA but aren’t subscribed to a tier with RBAC enabled, please get in touch with our sales team to upgrade your subscription.
If you’re a current enterprise paying user who would like more information about FOSSA RBAC, please visit our docs or contact your customer success representative.