If you’re reading this blog, it’s safe to assume that you’ve heard of the Log4J vulnerability “Log4Shell” and maybe even had a week or two ruined by the fallout.
In case you need a refresher, two critical-severity Remote Code Execution vulnerabilities were recently discovered in Log4J (coined “Log4Shell”), sending the software industry into a frenzy trying to identify and mitigate what is being called the worst vulnerability in the last decade. Following this, on Dec. 18, a third, less severe Denial of Service vulnerability was released, leading to another Log4J-filled weekend.
At FOSSA, we’ve been working hard to ensure that our users are quickly able to quickly detect and mitigate the Log4J vulnerabilities at scale. Today, we want to make it even easier for everyone — even if you’re not a FOSSA customer — to detect Log4Shell in their code.
Below, we provide easy detection and mitigation capabilities for fixing
- CVE-2021-44228, the original Log4J vulnerability that captured global headlines, discovered on Dec. 9
- CVE-2021-45046, discovered Dec. 14
- CVE-2021-45105, the Log4J denial of service vulnerability discovered Dec. 18
WATCH: On-Demand Webinar | An Interactive Exploration of the Log4J Vulnerability
How to Quickly Detect the Log4J Vulnerability (Log4Shell)
The FOSSA team has released an update to our CLI to help anyone detect Log4Shell in their code. As of this writing, you can now use the FOSSA CLI to detect Log4J vulnerabilities in your code with no account required.
To get started, follow our installation guide for FOSSA CLI.
Then, to detect Log4J Vulnerabilities in your project, run fossa log4j in your project root directory.
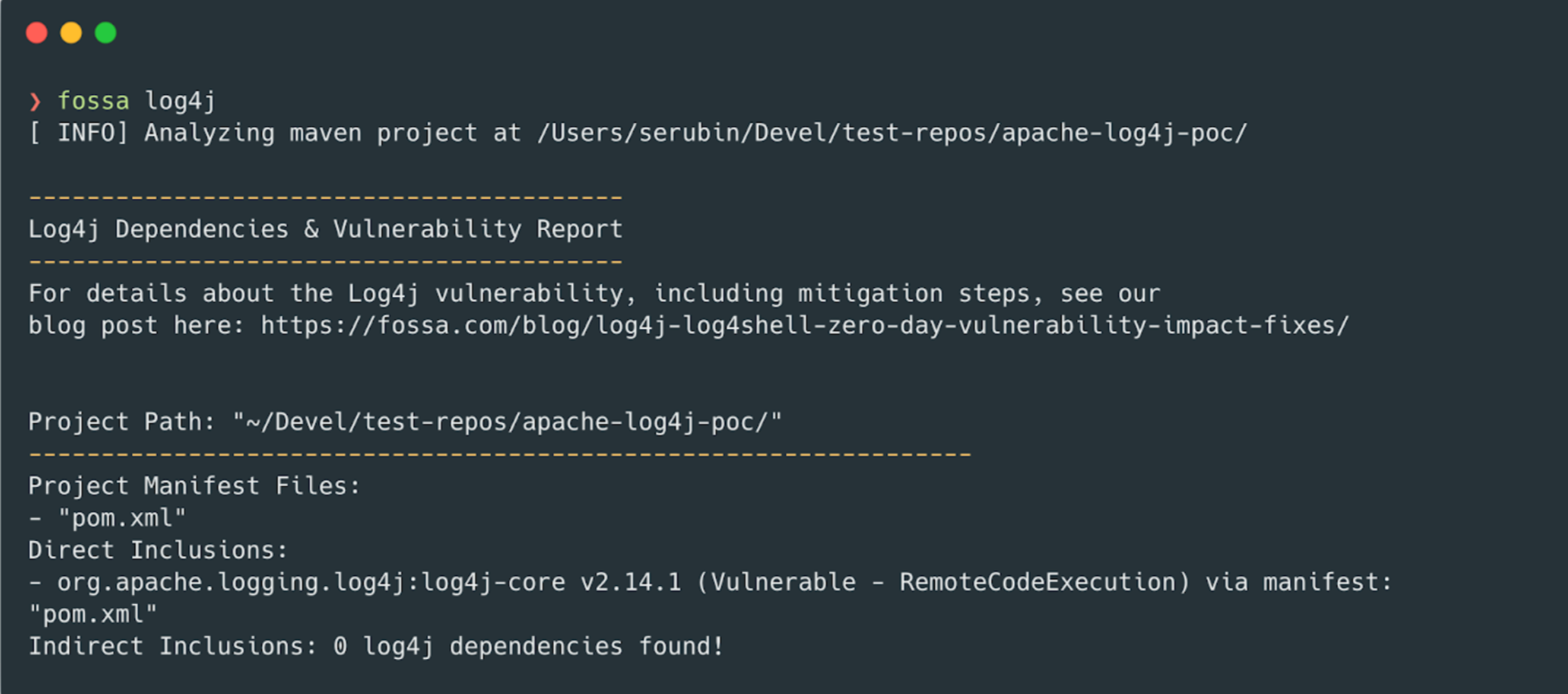
Our CLI’s Log4J command will provide you with all found Log4J vulnerabilities in direct dependencies and indirect (transitive) dependencies, as well as how they were included in your project.
DOWNLOAD: The Log4Shell Remediation Guide
How to Remediate Log4Shell and Log4J Vulnerabilities
The most surefire way to mitigate Log4J vulnerabilities is to upgrade. In instances when this is not possible, there are several alternate options available. Here is how we’d suggest you approach various remediation paths.
Upgrading a Vulnerable Version
At a minimum, FOSSA recommends upgrading to version 2.16.0 or higher to mitigate the critical RCE vulnerabilities.
To fix all notable vulnerabilities discovered in the last few weeks (including the DoS Vulnerability: CVE-2021-45105, which impacts 2.16.0), it's recommended to upgrade to 2.17.0 or higher. (The most recent version, 2.17.1, was released on Dec. 28.)
Replacing Affected Classes (for Releases from 2.0 to 2.10.0)
If upgrading is not possible, you can remove affected classes by using the following commands:
- Remove the LDAP class from Log4J by running the following command:
zip -q -d log4j-core-*.jar org/apache/logging/log4j/core/lookup/JndiLookup.class - Also remove:
JndiManager,JMSAppender,SMTPAppender
Disabling JDNI Lookups (for Log4J >=2.10)
If you are on a version of Log4J newer than 2.10.0, you can disable JNDI lookups using the following settings:
- System property
LOG4J_FORMAT_MSG_NO_LOOKUPStotrue - OR Environment variable
log4j2.formatMsgNoLookupstotrue - Note: JNDI lookups are disabled by default in version
2.16.0and newer
Mitigation via JVM settings is no longer possible. Other mitigations are still effective.
Automating Vulnerability Management with FOSSA
FOSSA's Vulnerability Management solution helps teams identify and remediate vulnerabilities like the ones impacting Log4J. For more information on bringing FOSSA to your organization, please click here and fill out the form. Our team will then be in touch with you shortly.