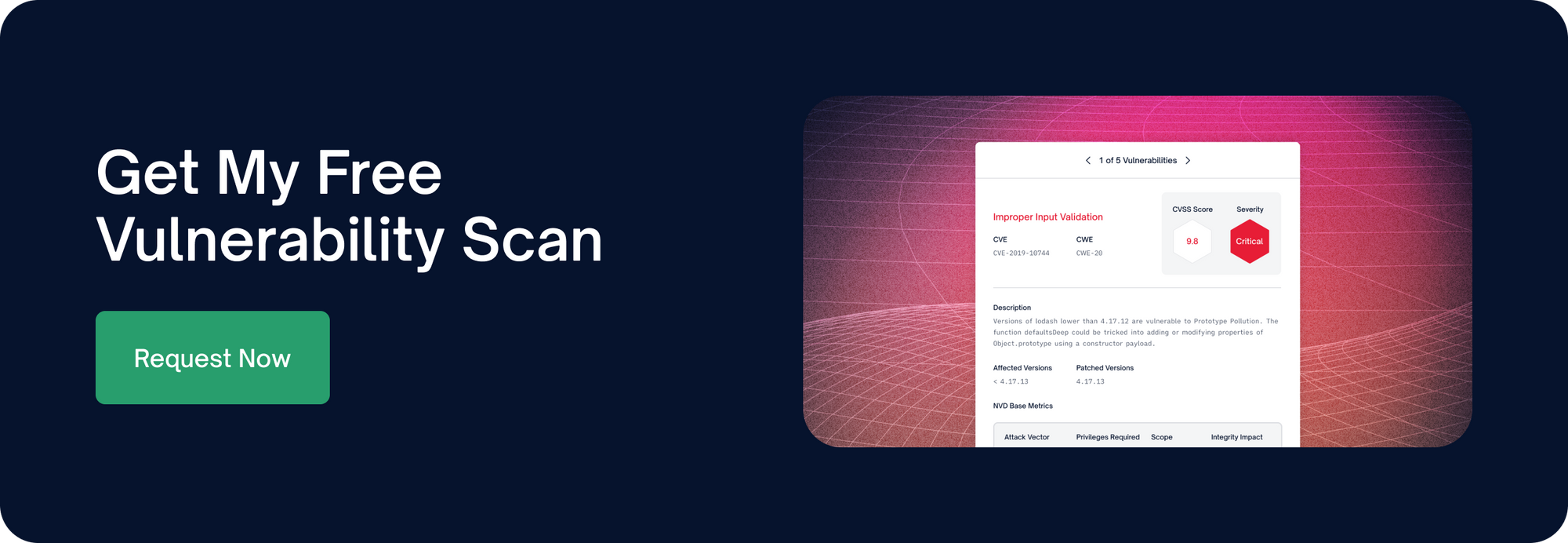
Yesterday, a third recent vulnerability was discovered in the popular Java logging library Log4J. The new vulnerability is now being tracked as CVE-2021-45105, It follows the two other vulnerabilities that were disclosed in recent weeks: CVE-2021-44228 (the original Log4J vulnerability that captured global headlines, discovered on Dec. 9) and CVE-2021-45046 (Dec. 14).
The latest vulnerability affects Log4J version 2.16.0 and versions prior via a Denial of Service Attack. This exploit has been assigned a CVSS severity score of Medium - 5.9. Log4J versions 2.0-alpha1 through 2.16.0 are vulnerable to this Denial of Service attack, which is triggered through uncontrolled recursion from self-referential lookups.
To fix all notable vulnerabilities discovered in the last few weeks (including the DoS Vulnerability), it's recommended to upgrade to 2.17.0 or higher. (The most recent version, 2.17.1, was released on Dec. 28.)
Impact of the New Log4J DoS Vulnerability
When successfully exploited, this vulnerability may allow for attackers to craft malicious input data that contains a self-referential lookup to execute an uncontrolled recursive lookup. This results in a StackOverflow Error, which will ultimately terminate the process. This vulnerability only occurs when logging configurations use non-default Pattern Layouts with a Context Lookup (i.e. ${ctx:username) that captures unsanitized user input.
How the New Log4J DoS Vulnerability Works
Unrelated to the previous issues with JNDI, this Denial of Service attack has been living in Log4J since release 2.x.x. Since the initial versions of Log4J 2, the library did not protect against uncontrolled recursion from self-referential lookups. When logging uses non-default Pattern Layouts with a Context Lookup, an attacker with control over Thread Context Map input data can provide malicious input data that contains a malicious recursive lookup.
DOWNLOAD: The Log4Shell Remediation Guide
For example, the Pattern Layout of ${localVariable}${ctx:username} could be vulnerable when provided with a malicious input to username. When provided with input to username such as ${${::-${::-$${::-j}}}} (from the initial PoC via @vxunderground, the result would be a denial of service and application crash.
Fixing the New Log4J DoS Vulnerability
While this is a high-severity vulnerability, it requires a very specific configuration to exploit. The surefire way to mitigate this issue is to upgrade to a fixed version of Log4J. If you are using any version of Log4J 2.x, including 2.0.0-alpha1 through 2.16.0, we recommend upgrading to 2.17.0 or higher. (The most recent version, 2.17.1, was released on Dec. 28.)
However, if this is not possible, you should ensure that your application is not using any Context Lookups within logs and remove any instances of Context Lookups if they exist. At present, FOSSA is not aware of any uses of this exploit in the real world and there has been no evidence to suggest any campaigns of this vulnerability (unlike the previous two exploits). However, FOSSA still recommends upgrading if you are able.
FOSSA's Vulnerability Management solution helps teams identify and remediate vulnerabilities like the ones impacting Log4J. For more information on bringing FOSSA to your organization, please click here and fill out the form. Our team will then be in touch with you shortly.


