Earlier this month, a new remote code execution vulnerability impacting the Apache Commons Text library was disclosed: Text4Shell. Text4Shell has since been assigned a 9.8 (out of 10) severity rating by the National Vulnerability Database, meaning it falls into the “critical” category.
Text4Shell impacts Apache Commons Text Versions 1.5-1.9 inclusive, though there are conditions around its exploitability which we’ll cover later in this article. The recommended remediation is to upgrade to Apache Commons Text Version 1.10.
Text4Shell was discovered and disclosed by GitHub threat analyst Alvaro Munoz.

Text4Shell Details and Comparisons to Log4Shell
Text4Shell impacts the Apache Commons Text library, which is a common Java library providing lots of utilities for working with strings. One feature that Apache Commons Text provides is string substitution, where the user can replace certain bits of text with another. A common way of dynamically creating strings is using something called an interpolator, which is used to look up values. Apache Commons Text provides a number of these interpolators by default.
Text4Shell is a vulnerability that occurs with certain default interpolators in versions 1.5 through 1.9 in Apache Commons Text. String interpolation is a common threat vector in applications and is something any developer should be aware of.
The affected interpolators are:
script: used to evaluate expressions using the JVM script execution engine (javax.script)dns: used to resolve DNS recordsurl: used to request information from a URL
GitHub's security blog describes the issue as follows
The
StringSubstitutorwhen used with the default interpolators (StringSubstitutor.createInterpolator()) will perform string lookups that may lead to arbitrary code execution.In particular, if untrusted data flows into the
StringSubstitutor.replace()orStringSubstitutor.replaceIn()methods, an attacker will be able to use theScriptStringLookupto trigger arbitrary code execution.
As mentioned, Text4Shell is a remote code execution vulnerability, which is part of why it’s drawn comparisons to Log4Shell. But the early indications are that Text4Shell is far less likely to become widespread than Log4Shell. This is because Log4Shell occurred in a method expected to consume data, which is expected to be trustworthy. Text4Shell exists in a method which is intended to be used for string interpolation, and thus developers are more likely to write their own safeguards when consuming the data.
In order to be affected by Text4Shell, the following conditions must be met:
- The application is using Apache Commons Text, version 1.5 through 1.9 inclusive
- The application imports
org.apache.commons.text.StringSubstitutorand uses one of the following default interpolators with the default configurationdnsscripturl
Apache’s security team offered additional context on the Log4Shell vs. Text4Shell comparison in a recent blog, which reads in part:
This issue is different from Log4Shell (CVE-2021-44228) because in Log4Shell, string interpolation was possible from the log message body, which commonly contains untrusted input. In the Apache Common Text issue, the relevant method is explicitly intended and clearly documented to perform string interpolation, so it is much less likely that applications would inadvertently pass in untrusted input without proper validation.
How to Find and Fix Text4Shell
FOSSA Vulnerability Management subscribers can use our product to easily detect vulnerable versions of Apache Commons. Simply do the following:
- Import your project using our CLI tool (preferred, most accurate) or using our Quick Import tool (easiest to use for non-technical users)
- Navigate to your project in the UI and view your security issues:
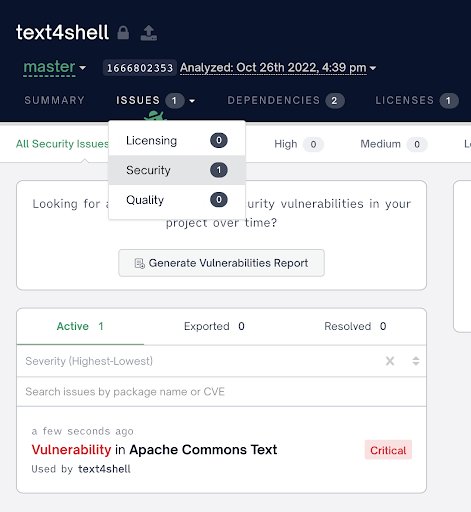
OR run fossa test
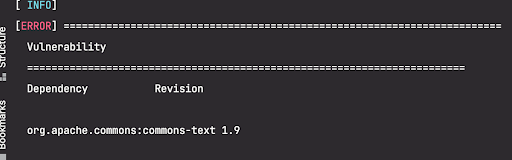
FOSSA license compliance or free users can still check for vulnerable versions of Apache Commons Text by using our API or by searching your projects’ dependency lists manually.
As mentioned, if you are using a vulnerable version of Apache Text Commons, it’s recommended that you update to the safe Version 1.10.
If you aren’t currently a FOSSA user, you can get started by selecting one of the following options:
- Request a demo of FOSSA Vulnerability Management (recommended for larger organizations)
- Sign up for the free version of FOSSA (recommended for individuals and small organizations)
FOSSA customer support engineer Sara Beaudet and software engineer Andrew Dailey contributed to this post.


